In today’s fast-paced digital world, Nigerian businesses are increasingly moving online — from small e-commerce stores to large financial institutions. While this shift brings growth opportunities, it also opens doors to cyber threats that can disrupt operations, damage reputations, and cause financial loss. The good news? With the right cybersecurity practices, businesses can protect themselves […]
In today’s digital landscape, the most dangerous threats to cybersecurity don’t always come from outside the organization — sometimes, they’re already inside. Insider attacks are a growing concern, especially for businesses that handle sensitive data or operate in highly regulated industries. As cyber defense mechanisms evolve to block external threats, malicious or negligent insiders have […]
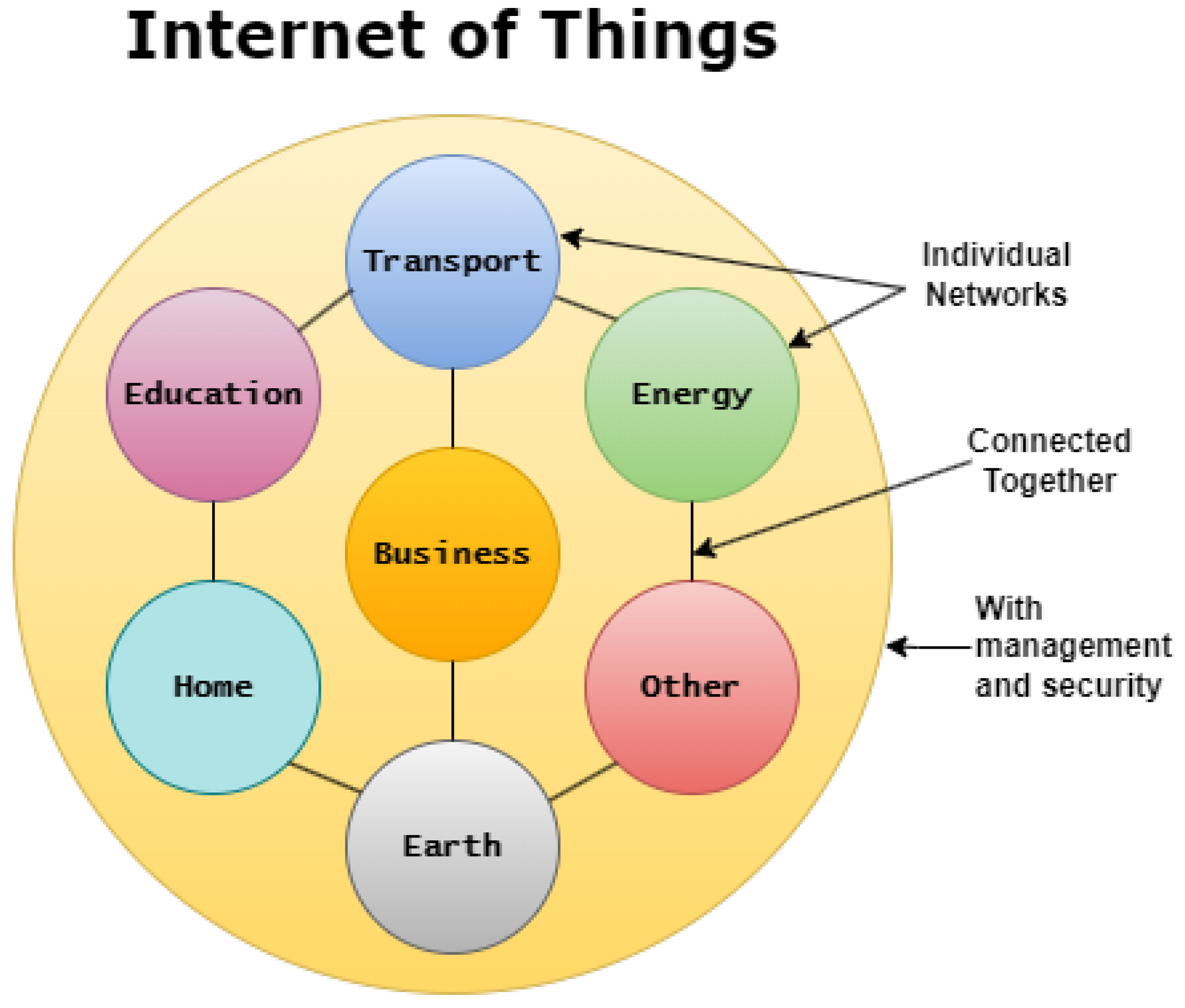
The rapid adoption of Internet of Things (IoT) devices in both personal and enterprise environments has transformed the way we live and work. From smart thermostats and connected CCTV systems to industrial sensors and healthcare monitors, IoT devices bring convenience, automation, and efficiency. However, this growing ecosystem also introduces serious security concerns. Why IoT Devices […]
In a rapidly evolving digital world where cyber threats are growing more sophisticated, ethical hacking has emerged as a critical strategy for identifying and addressing vulnerabilities before malicious attackers can exploit them. Ethical hacking—also known as penetration testing or white-hat hacking—involves authorized security experts simulating real-world cyberattacks to uncover weaknesses in systems, networks, and applications. […]
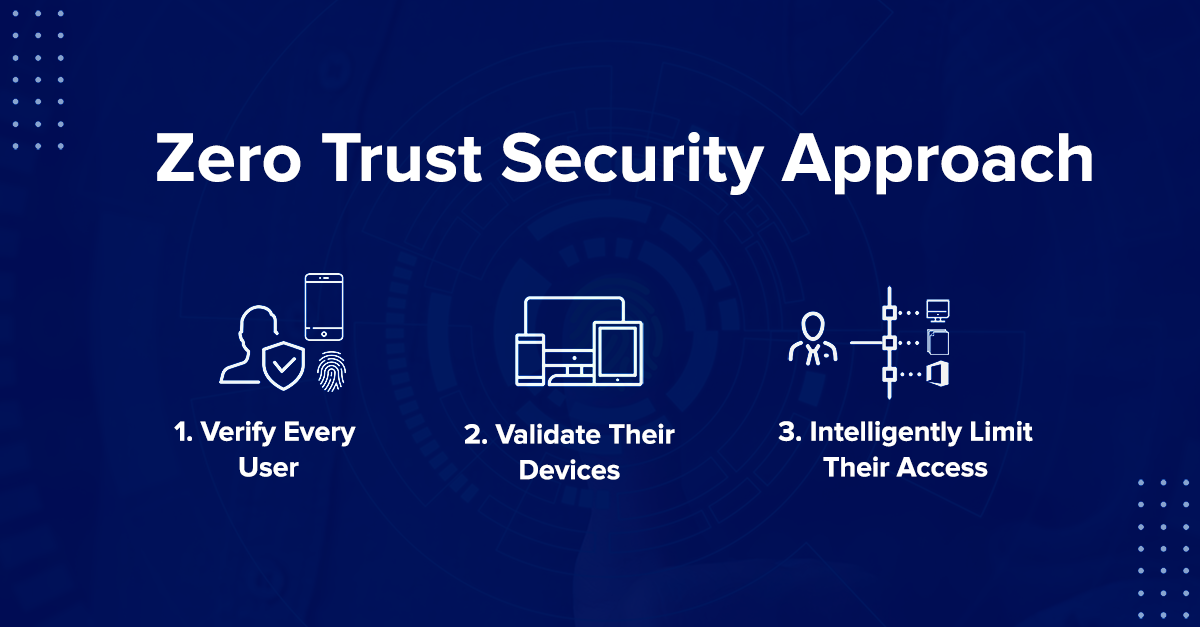
As cyber threats become more sophisticated in 2025, traditional security models no longer offer the protection that businesses need. The Zero Trust security model is emerging as a powerful defense mechanism—especially for organizations handling sensitive data or operating in hybrid environments. What is Zero Trust Security? Zero Trust is a cybersecurity framework that operates on […]
Introduction In today’s fast-paced digital landscape, cloud computing has become an essential component of modern businesses. Companies of all sizes leverage cloud technologies to enhance scalability, efficiency, and security while reducing operational costs. At i4 Tech Integrated Services, we help businesses harness the power of cloud computing for web design, app development, IT solutions, and […]
How to Protect Your IT Systems and Data from Ransomware Attacks Ransomware attacks have become one of the most significant cybersecurity threats to businesses and individuals. These attacks involve malicious software that encrypts files and demands a ransom for their release. To safeguard your IT systems and data, it is crucial to implement strong security […]
Cloud Security Best Practices: Safeguarding Your Data in the Cloud As businesses increasingly shift their operations to the cloud, ensuring the security of sensitive data and applications has never been more important. Cloud computing offers unparalleled flexibility, scalability, and cost-efficiency, but it also introduces new challenges when it comes to data protection and cybersecurity. Data […]
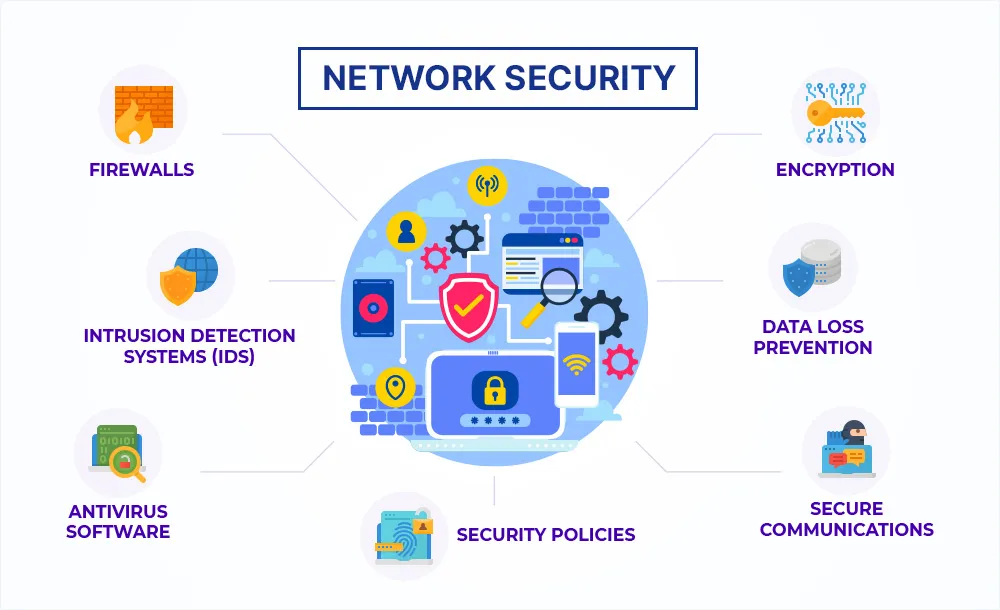
In today’s digital-first world, businesses rely on robust and secure networks to ensure seamless communication, data transfer, and operational efficiency. i4 Tech Integrated Services provides Enterprise Network Management Solutions designed to optimize network performance, enhance security, and support business scalability. What Is an Enterprise Network Management Solution? Enterprise Network Management Solutions involve centralized monitoring, control, […]