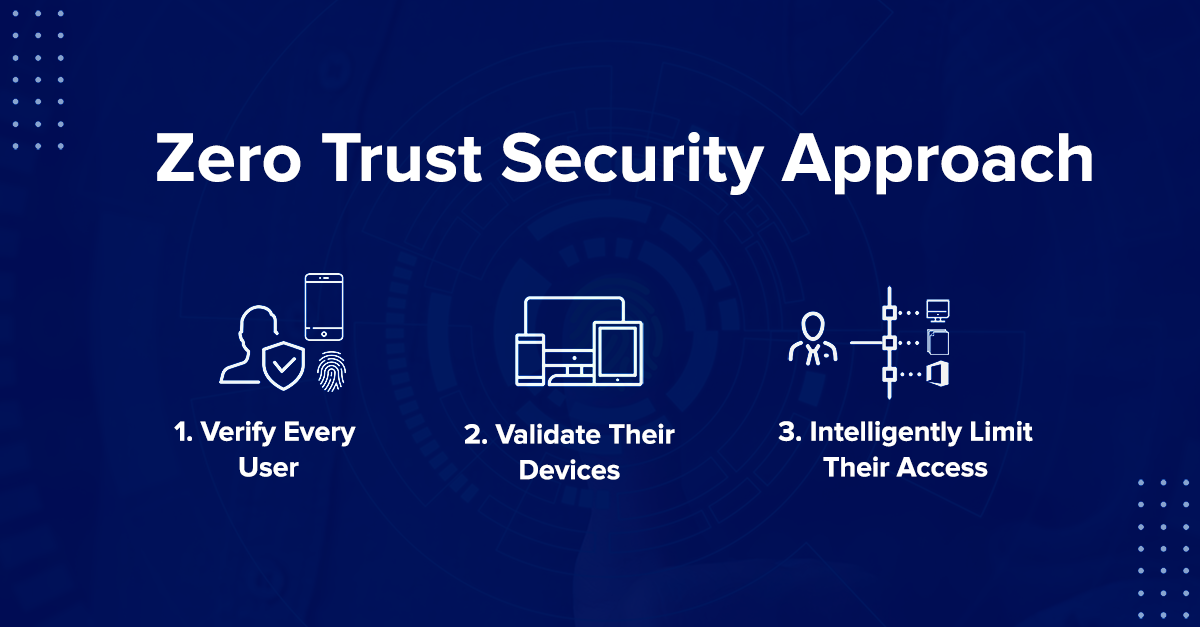
As cyber threats become more sophisticated in 2025, traditional security models no longer offer the protection that businesses need. The Zero Trust security model is emerging as a powerful defense mechanism—especially for organizations handling sensitive data or operating in hybrid environments. What is Zero Trust Security? Zero Trust is a cybersecurity framework that operates on […]
In today’s hyper-connected digital world, cybersecurity is no longer just an IT issue—it’s a business necessity. As we move further into 2025, the importance of cybersecurity has reached an all-time high. At i4 Tech Integrated Services, we believe that understanding and investing in cybersecurity is crucial to protect not just data, but reputation, operations, and […]
How to Detect and Prevent Phishing Attacks in IT Phishing attacks are one of the most common and dangerous cyber threats faced by individuals and organizations today. These attacks involve cybercriminals posing as legitimate entities to deceive victims into revealing sensitive information, such as login credentials, financial details, or personal data. Understanding how to detect […]
How to Protect Your IT Systems and Data from Ransomware Attacks Ransomware attacks have become one of the most significant cybersecurity threats to businesses and individuals. These attacks involve malicious software that encrypts files and demands a ransom for their release. To safeguard your IT systems and data, it is crucial to implement strong security […]