How Cybersecurity Audits Protect Your Business from Invisible Threats Cyber threats are no longer limited to large corporations. Small and medium-sized businesses are increasingly targeted because of weak security systems and limited awareness. A cybersecurity audit is one of the most effective ways to identify and eliminate these hidden risks before they cause serious damage. […]
Cyber Resilience vs Cybersecurity: What African Businesses Must Know for 2025 While cybersecurity focuses on preventing attacks, cyber resilience ensures your business can recover when — not if — an attack happens. This difference is crucial for African enterprises adapting to rapid digitization. Cyber resilience integrates prevention, detection, response, and recovery. It’s not just about […]
Quantum-Safe Networks: Preparing for Post-Quantum Cryptography in Business Quantum computing is rising — and it will break today’s encryption in seconds. Businesses must prepare for quantum-safe cybersecurity or risk total data compromise. ⚠️ The Threat Traditional encryption relies on mathematical complexity — quantum computers solve those problems instantly. This means: ✅ What Businesses Should Do […]
The Power of Cloud Security: How Businesses Are Protecting Their Data in the AI Era As companies migrate to cloud platforms, data security has become a top priority. In 2025, businesses aren’t just storing data in the cloud — they’re securing it using AI-driven cybersecurity and multi-layered encryption systems. How Cloud Security Works Cloud security […]
Why Cloud Security Misconfigurations Are the Biggest Threat in 2025 In 2025, cloud computing dominates business IT infrastructure, but one persistent issue has emerged as the largest security risk—cloud misconfigurations. What Are Cloud Misconfigurations? These occur when cloud resources (servers, databases, storage) are set up incorrectly, leaving them vulnerable to unauthorized access or data leaks. […]
For small and medium-sized enterprises (SMEs), cybersecurity is often seen as something only big corporations need to worry about. Unfortunately, cybercriminals increasingly target SMEs because they assume smaller businesses have weaker defenses. A single breach can lead to financial loss, reputational damage, and operational disruption. At i4 Tech Integrated Services, we believe that strong cybersecurity […]
In today’s digital era, businesses rely heavily on data and IT systems to operate efficiently. But unexpected events—natural disasters, cyberattacks, hardware failures, or human error—can disrupt operations and threaten the integrity of critical data. Without a robust disaster recovery and business continuity plan, even a minor incident can lead to significant financial losses and reputational […]
In today’s fast-paced digital world, Nigerian businesses are increasingly moving online — from small e-commerce stores to large financial institutions. While this shift brings growth opportunities, it also opens doors to cyber threats that can disrupt operations, damage reputations, and cause financial loss. The good news? With the right cybersecurity practices, businesses can protect themselves […]
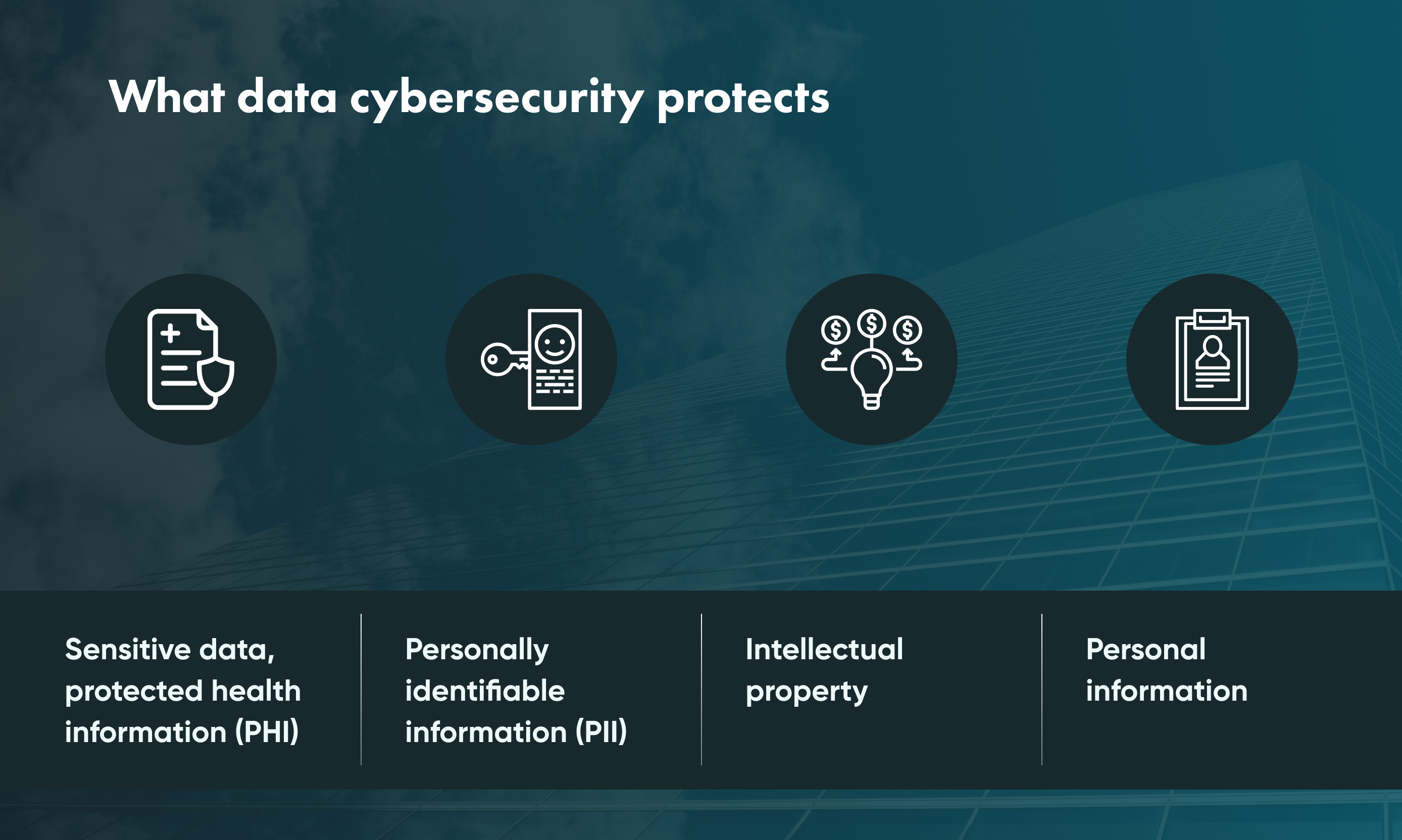
In an age where data is one of the most valuable business assets, organizations are under increasing pressure to manage it responsibly. Two critical frameworks—data governance and regulatory compliance—have emerged as essential to managing data effectively, ethically, and legally. While they serve different purposes, their intersection is where organizations find clarity, control, and credibility in […]
How Cybersecurity Audits Protect Your Business from Invisible Threats As cyber threats grow in sophistication, businesses must stay proactive. A cybersecurity audit is not a luxury—it’s a necessity for every organization that handles sensitive data. What Is a Cybersecurity Audit? A cybersecurity audit is a systematic evaluation of your organization’s digital defenses. It assesses vulnerabilities, […]