As we move into the second half of the decade, Web3 technologies are maturing—and one of its most promising applications is Decentralized Identity (DID). In a time of rampant data breaches and increasing surveillance, decentralized identity may hold the key to restoring user control online. What Is Decentralized Identity? DID allows individuals to own and […]
In today’s fast-evolving digital environment, Nigerian businesses face increasing threats from cybercriminals. While investing in cutting-edge security infrastructure is crucial, many organizations overlook one critical factor: the human element. Employees can be either the strongest line of defense—or the weakest link. Building a culture of cybersecurity awareness is no longer optional; it’s essential. Why Cybersecurity […]
As cyber threats evolve in complexity and frequency, organizations are increasingly turning to artificial intelligence (AI) and automation to bolster their cybersecurity defenses. These technologies offer the potential to detect threats faster, respond more effectively, and reduce the burden on human analysts. However, their integration also comes with unique risks that businesses must understand and […]
In today’s digital landscape, the most dangerous threats to cybersecurity don’t always come from outside the organization — sometimes, they’re already inside. Insider attacks are a growing concern, especially for businesses that handle sensitive data or operate in highly regulated industries. As cyber defense mechanisms evolve to block external threats, malicious or negligent insiders have […]
In today’s digital-first economy, small businesses in Nigeria and across the globe are becoming prime targets for cybercriminals. Many entrepreneurs assume they’re too small to be noticed — but that assumption can be costly. Fortunately, protecting your business doesn’t have to break the bank. With the right strategies, small businesses can implement affordable cybersecurity solutions […]
As cyber threats continue to evolve in complexity and scale, 2025 is shaping up to be a defining year in the cybersecurity landscape. From AI-driven attacks to quantum computing challenges, organizations must embrace new technologies to stay ahead of adversaries. Here are the top emerging cybersecurity technologies to watch in 2025: 1. AI-Powered Threat Detection […]
In today’s digital landscape, where cyber threats are evolving rapidly, having a well-defined incident response plan is no longer optional—it’s essential. Whether you’re running a small business or managing IT for a large enterprise, a cybersecurity breach can have devastating financial and reputational consequences. That’s why preparing for incidents before they happen is key. What […]
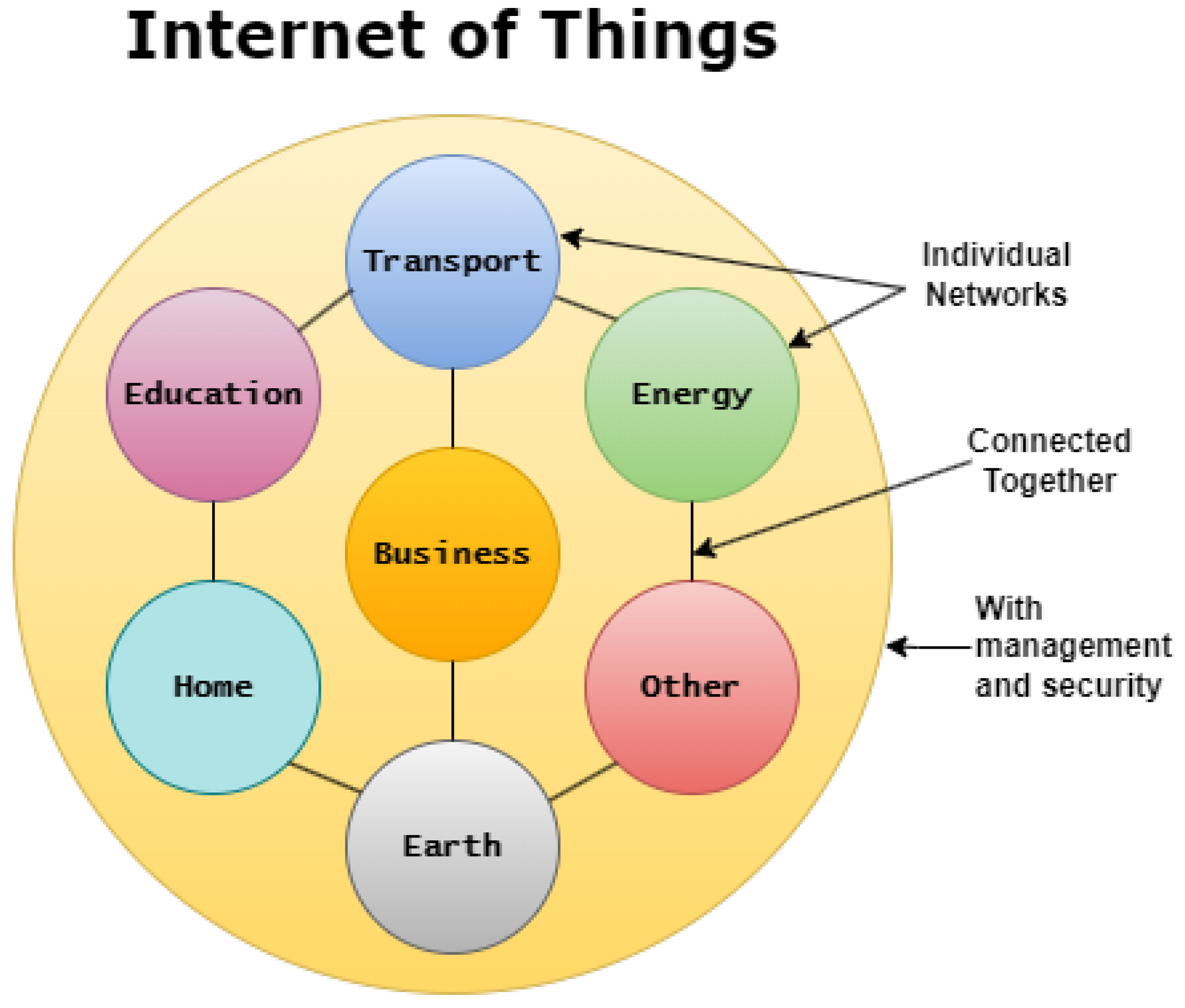
The rapid adoption of Internet of Things (IoT) devices in both personal and enterprise environments has transformed the way we live and work. From smart thermostats and connected CCTV systems to industrial sensors and healthcare monitors, IoT devices bring convenience, automation, and efficiency. However, this growing ecosystem also introduces serious security concerns. Why IoT Devices […]
In today’s hyper-connected world, cybercriminals are no longer just exploiting software vulnerabilities—they’re exploiting human behavior. Social engineering is a growing cybersecurity threat that involves manipulating individuals into divulging confidential or personal information. Unlike traditional hacking methods, social engineering doesn’t rely on complex code but on psychological tricks. What Is Social Engineering? Social engineering is the […]
In a rapidly evolving digital world where cyber threats are growing more sophisticated, ethical hacking has emerged as a critical strategy for identifying and addressing vulnerabilities before malicious attackers can exploit them. Ethical hacking—also known as penetration testing or white-hat hacking—involves authorized security experts simulating real-world cyberattacks to uncover weaknesses in systems, networks, and applications. […]