In today’s data-driven world, organizations are generating vast amounts of information daily. From customer records to operational metrics, businesses need reliable, scalable, and cost-effective storage solutions. Yet many companies struggle with managing complex storage systems, rising costs, and data accessibility challenges. At i4 Tech Integrated Services, we simplify data storage, providing businesses with efficient solutions […]
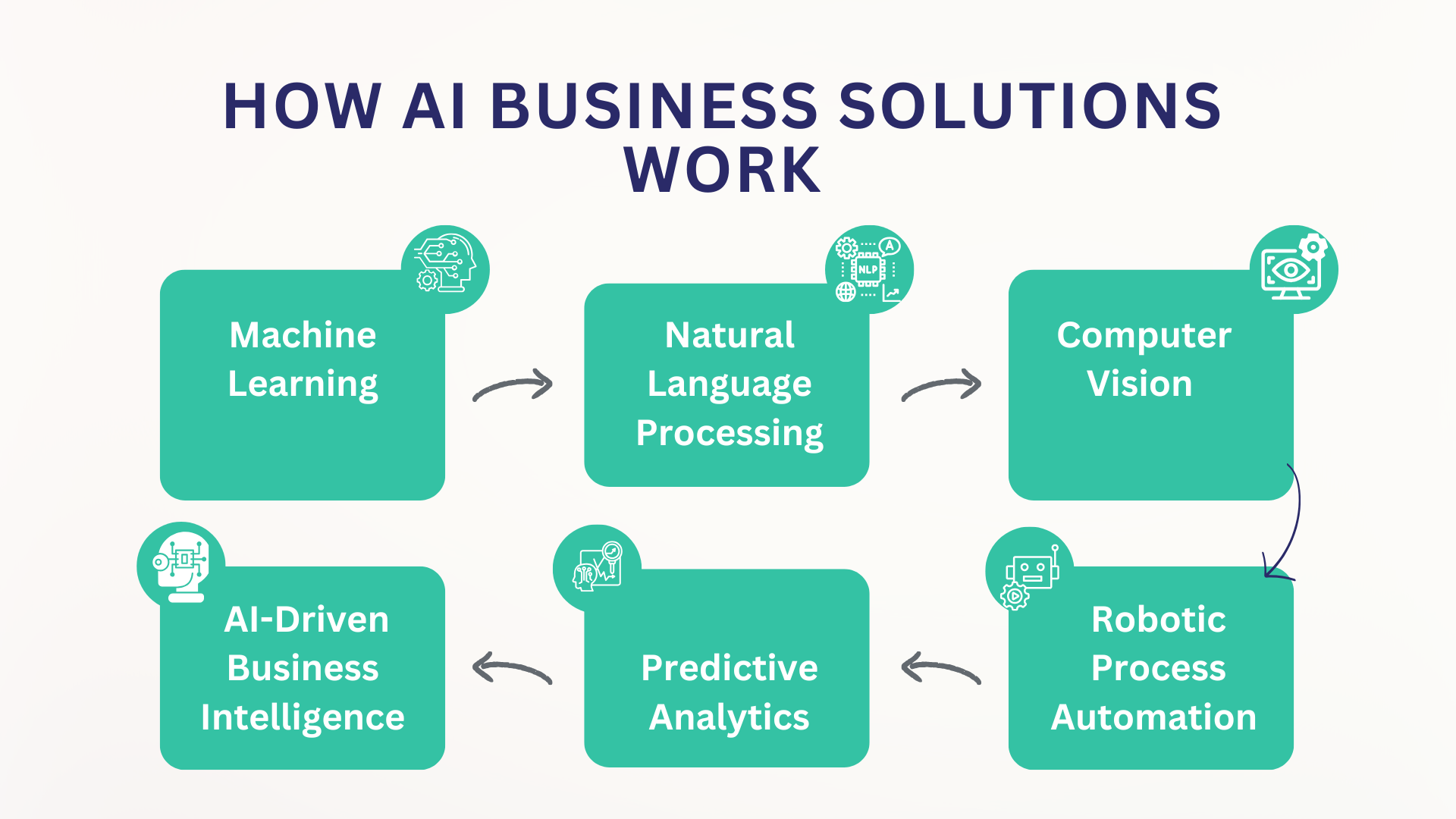
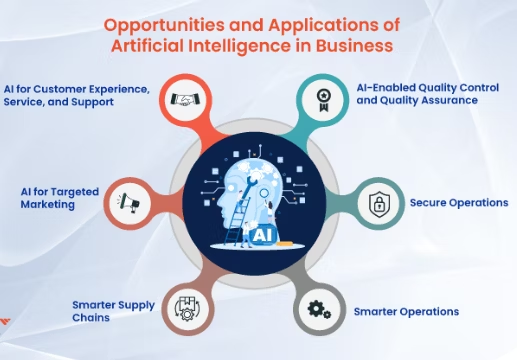
In today’s competitive business landscape, data is power—but only if organizations know how to harness it effectively. Artificial Intelligence (AI) and advanced analytics have become essential tools for businesses looking to unlock insights, optimize operations, and drive growth. At i4 Tech Integrated Services, we specialize in creating custom AI and analytics solutions that empower businesses […]
In every industry, businesses are generating more data than ever before. But simply collecting data isn’t enough—what matters is how effectively that data is managed and applied. Poor data management can slow down operations, increase costs, and create confusion across teams. On the other hand, intelligent data management can streamline workflows, improve efficiency, and drive […]
In today’s digital-first world, cybersecurity is no longer optional—it’s essential. Every organization, regardless of size, is a potential target for cybercriminals. From ransomware attacks to data breaches, the risks are increasing daily. What’s worse, a single breach can cost businesses not only financially but also in lost reputation and customer trust. At i4 Tech Integrated […]
Breaking Down Zero Trust Security for SMEs Cybersecurity threats are growing, and traditional perimeter-based defenses are no longer enough. This is where Zero Trust Security comes in—especially critical for small and medium enterprises (SMEs) in 2025. Core Principles of Zero Trust Why SMEs Need Zero Trust Practical Steps for SMEs
As we approach 2025, the cybersecurity landscape is evolving faster than ever. Businesses, governments, and individuals are facing increasingly sophisticated cyber threats, fueled by rapid technological advancements and a growing digital economy. Understanding global cybersecurity trends is critical for staying ahead of attackers and safeguarding digital assets. At i4 Tech Integrated Services, we provide insights […]
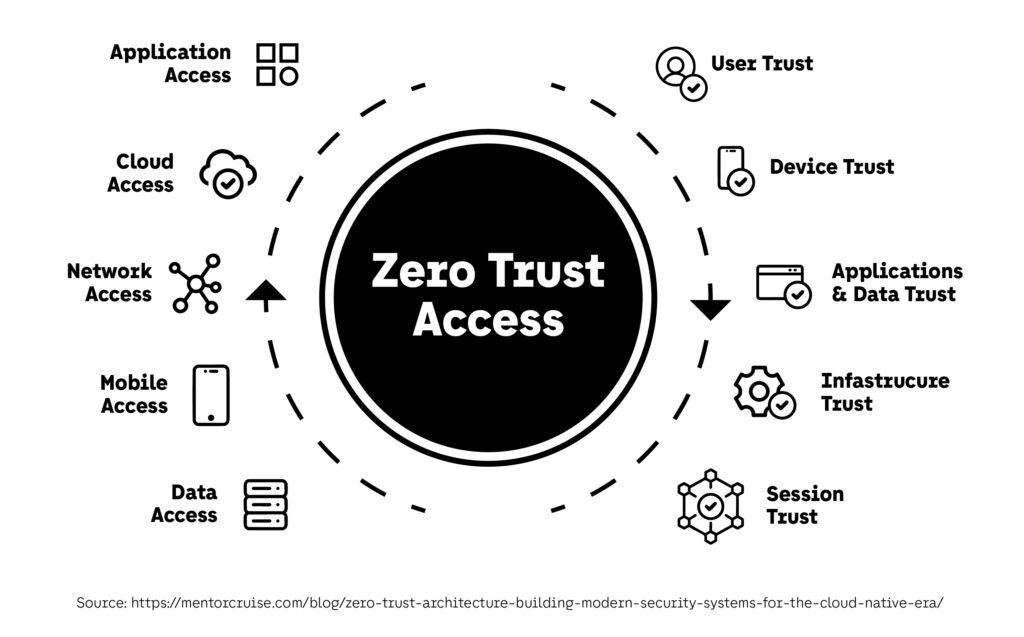
As businesses adopt cloud computing, remote work, and hybrid IT environments, traditional perimeter-based security models are no longer sufficient. In 2025, Zero Trust Architecture (ZTA) has emerged as the gold standard for enterprise security, ensuring that every user, device, and application is continuously verified before granting access to sensitive resources. At i4 Tech Integrated Services, […]
In 2025, cybersecurity is no longer just about technology—it’s about people. While firewalls, AI-based threat detection, and encryption protect systems, human error remains the leading cause of cyber breaches. From falling for phishing scams to weak password practices, the human factor is the weakest link in any organization’s cybersecurity chain. At i4 Tech Integrated Services, […]
In 2025, governments face an unprecedented level of cyber threats targeting national infrastructure. Critical systems—including energy grids, transportation networks, communication systems, and public services—are increasingly digitized, making them attractive targets for cybercriminals, hacktivists, and state-sponsored actors. The consequences of a successful attack can range from service disruptions to economic loss and even threats to public […]
Healthcare systems are among the most critical infrastructures in any country. With the rapid adoption of digital health records, telemedicine, IoT medical devices, and cloud-based healthcare solutions, the healthcare sector is more connected than ever. While these technologies improve patient care and operational efficiency, they also introduce significant cybersecurity risks. In 2025, safeguarding healthcare data […]