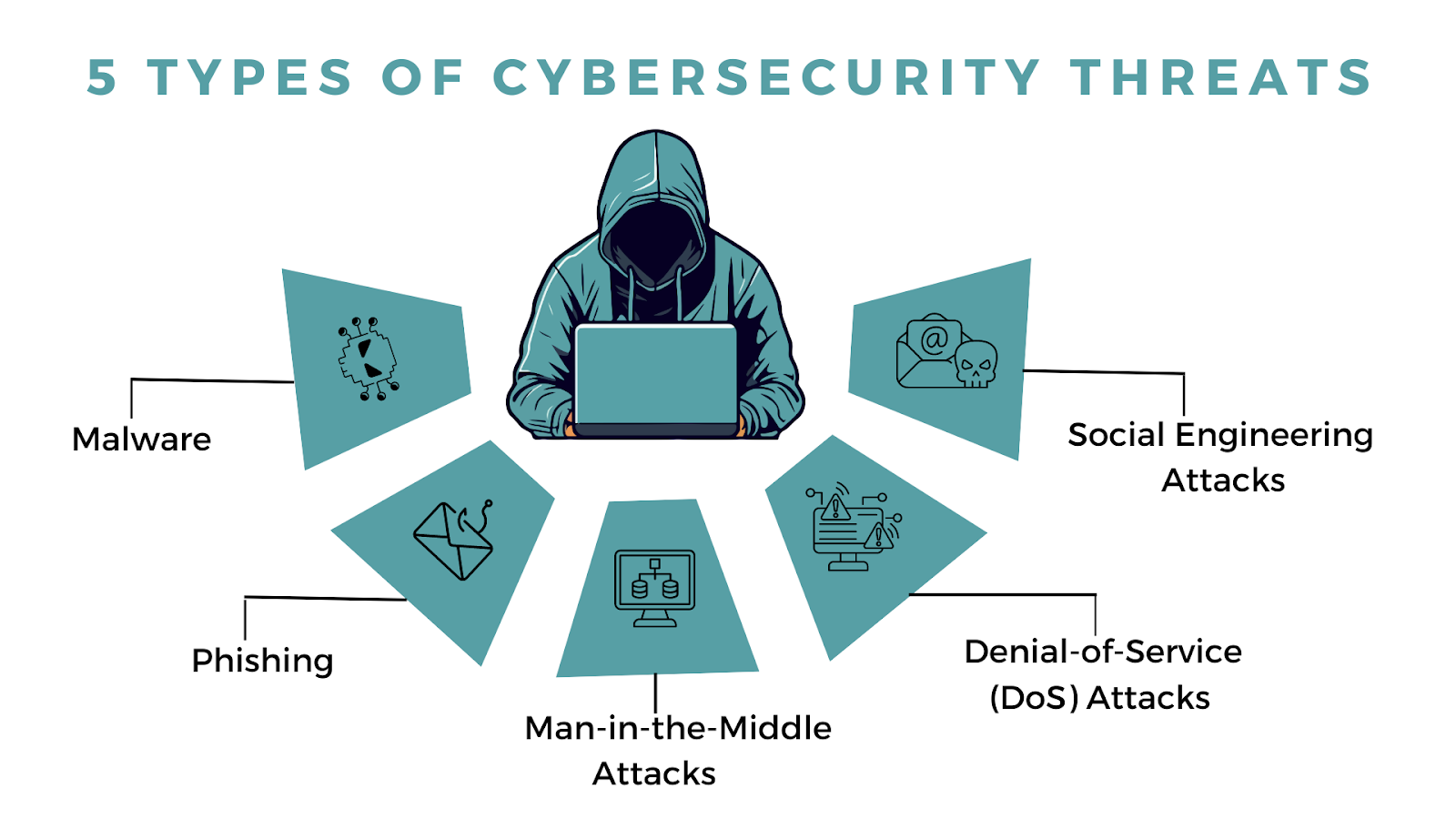
How Cybersecurity Audits Protect Your Business from Invisible Threats Cyber threats are no longer limited to large corporations. Small and medium-sized businesses are increasingly targeted because of weak security systems and limited awareness. A cybersecurity audit is one of the most effective ways to identify and eliminate these hidden risks before they cause serious damage. […]
Quantum computing is one of the most revolutionary technologies shaping the future of computing. Unlike classical computers—which process information in bits (0 or 1)—quantum computers use qubits, which can be 0 and 1 at the same time. This makes them incredibly powerful. Why It Matters Quantum computers can solve complex problems impossible for today’s systems: […]
Cyber Resilience vs Cybersecurity: What African Businesses Must Know for 2025 While cybersecurity focuses on preventing attacks, cyber resilience ensures your business can recover when — not if — an attack happens. This difference is crucial for African enterprises adapting to rapid digitization. Cyber resilience integrates prevention, detection, response, and recovery. It’s not just about […]
The Power of Cloud Security: How Businesses Are Protecting Their Data in the AI Era As companies migrate to cloud platforms, data security has become a top priority. In 2025, businesses aren’t just storing data in the cloud — they’re securing it using AI-driven cybersecurity and multi-layered encryption systems. How Cloud Security Works Cloud security […]
In today’s fast-paced digital world, businesses can no longer rely on traditional methods alone to remain competitive. Customers expect faster services, smarter solutions, and seamless online experiences. To meet these expectations, businesses of all sizes must embrace digital transformation. But what exactly does “digital transformation” mean, and why does every business need a plan for […]
The world of work is changing faster than ever before. Thanks to Artificial Intelligence (AI) and automation, businesses of all sizes are discovering new ways to cut costs, improve efficiency, and deliver better customer experiences. But what does this shift really mean for business owners today? Is AI only for large corporations, or can small […]
In today’s fast-paced digital economy, businesses of all sizes depend on technology to run smoothly. Whether it’s managing customer data, processing payments, or communicating with clients, nearly every business activity is now digital. While this brings efficiency and growth, it also opens the door to cybersecurity risks. Cybercrime is no longer a problem reserved for […]
Why Businesses Fail Without Proper Data Backup Strategies Data is the lifeblood of modern business, yet many organizations continue to treat backup strategies as an afterthought. In 2025, cyberattacks, system failures, and human errors are common threats that can wipe out years of critical information in seconds. Businesses that fail to implement robust data backup […]
In today’s digital era, businesses rely heavily on data and IT systems to operate efficiently. But unexpected events—natural disasters, cyberattacks, hardware failures, or human error—can disrupt operations and threaten the integrity of critical data. Without a robust disaster recovery and business continuity plan, even a minor incident can lead to significant financial losses and reputational […]
In today’s fast-paced business environment, access to accurate and timely data is crucial for decision-making and operational efficiency. Yet, many organizations struggle with data silos, fragmented systems, and delayed insights that slow down their teams. At i4 Tech Integrated Services, we help businesses break down barriers to data accessibility, enabling teams to access the information […]