Zero Trust Architecture: The Future of Enterprise Security in 2025
As businesses adopt cloud computing, remote work, and hybrid IT environments, traditional perimeter-based security models are no longer sufficient. In 2025, Zero Trust Architecture (ZTA) has emerged as the gold standard for enterprise security, ensuring that every user, device, and application is continuously verified before granting access to sensitive resources.
At i4 Tech Integrated Services, we believe that embracing Zero Trust is essential for protecting businesses against increasingly sophisticated cyber threats.
What Is Zero Trust Architecture?
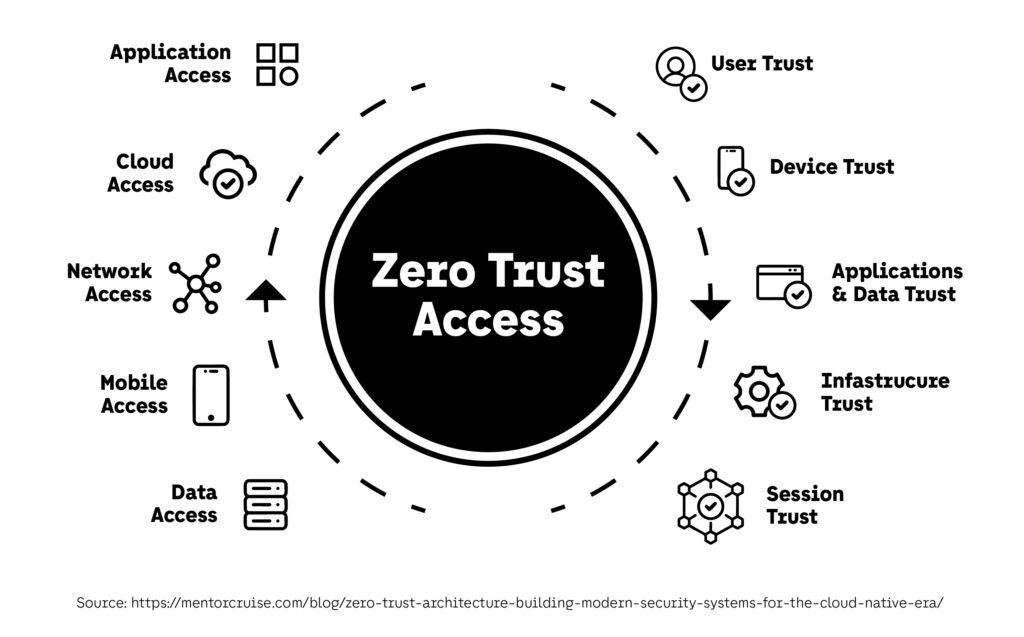
Zero Trust is a security model that operates on a simple principle: “Never trust, always verify.” Unlike traditional security models that assume everything inside the network is safe, Zero Trust treats all access attempts as potentially malicious, requiring strict verification before granting permissions.
Key components of ZTA include:
- Identity Verification: Ensuring every user is authenticated using strong methods like multi-factor authentication (MFA).
- Device Security: Verifying that devices comply with security policies before allowing network access.
- Micro-Segmentation: Dividing networks into smaller zones to limit lateral movement by attackers.
- Continuous Monitoring: Constantly analyzing traffic, behaviors, and access patterns for anomalies.
- Least Privilege Access: Users are only granted the minimum access necessary to perform their tasks.
Why Zero Trust Is Critical in 2025
- Rise of Remote Work: With employees accessing company resources from various locations and devices, perimeter-based security is insufficient.
- Cloud Adoption: Multi-cloud and hybrid cloud environments increase complexity and the need for granular access controls.
- Advanced Threats: AI-driven attacks, ransomware, and insider threats require a proactive, verification-based security approach.
- Regulatory Compliance: Zero Trust frameworks help organizations meet strict privacy and security regulations.
- Minimizing Breach Impact: Micro-segmentation and least privilege access prevent attackers from moving freely across networks if a breach occurs.
Implementing Zero Trust in Your Enterprise
- Start with Identity: Implement strong authentication methods and identity management systems.
- Secure Devices and Endpoints: Enforce compliance checks and endpoint security policies.
- Segment Networks: Limit internal access and monitor lateral movement.
- Continuous Monitoring and Analytics: Deploy AI-powered tools to detect anomalies in real time.
- Educate Employees: Promote awareness about access policies, MFA, and cybersecurity best practices.
The Future of Enterprise Security
In 2025, Zero Trust Architecture is no longer optional—it is a strategic requirement for enterprises aiming to stay secure in an increasingly digital and threat-prone environment. Organizations that implement ZTA effectively will benefit from stronger defenses, reduced breach risks, and enhanced compliance with global security standards.
Conclusion
Zero Trust transforms enterprise security from a reactive approach to a proactive, verification-first strategy. By continuously validating users, devices, and applications, businesses can secure sensitive data, prevent breaches, and build resilience against evolving cyber threats.
At i4 Tech Integrated Services, we help enterprises implement Zero Trust frameworks tailored to their operations, providing a future-ready security posture for 2025 and beyond.
Adopt Zero Trust today to ensure your enterprise stays secure tomorrow.

